AD Tier Model Overview
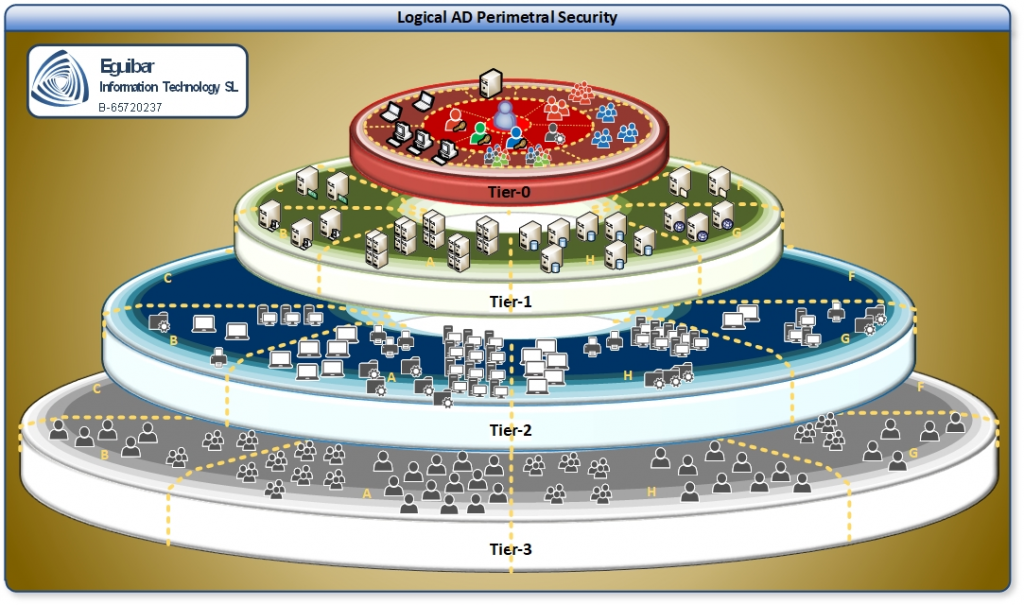
The "Active Directory Tier Model" is a logical separation of AD assets, having some kind of security boundaries in between. The idea is to protect the most valued identities within the active directory (Tier 0), while standard desktops and users (Tier2, and in some cases Tier 3) can surf the web, check their email, or access services and applications that reside on a different tier (Tier 1). Microsoft provides extensive information on the Tier Model. The implementation of such model will help significantly mitigate “Credential Theft” techniques as it could be “Pass-the-Hash” or “Pass-the-ticket”, which are the basis of todays majority security breaches.
In this article we will explore the Tier Model, its definitions, and some implementation tips.
Confusion might arise when speaking about the "Delegation Model"and the intimate relationship with the"Active Directory Tier Model". Well, this confusion disappears when we treat both models as a single one, having 2 different characteristic or phases. Each of these divisions focuses on specific topics, granting security to the other party. Microsoft has extensive documentation on the Tiering Model, and as a matter of fact, on the Securing Privileged Access document, on section “Security Privileged Access Roadmap: Stage 3” the Delegation Model request to update the model.
Delegation Model, the logical part
This Delegation Model does fits naturally onto the defined tiers, as explained earlier. Figure the model as the Role Based Access Control (RBAC). The tier model is a strict separation of assets and operational procedures to administer those. For example, managing a Tier0 asset (admin area), is a right that only a Tier0 semi-privileged account has. And only from a Tier0 privileged access workstation (PAW). Failing to maintain this segregation might expose identities. Following this idea, if a Tier2 administration has to manage a Tier1 asset, then he is not a Tier2 administrator anymore. He has to be consider as the most restrictive tier within its duties. Effectively a Tier1 administrator in this example, so he must use a Tier1 semi-privileged account and a Tier1 PAW.
Cross Areas or Cross Tiers
As explained before, the tier model is a strict separation of assets and operational procedures to administer those. This means that a Tier0 administrator must not be using a Tier1 or Tier2 account to perform his daily tasks. Neither should he be using a Tier1 or Tier2 PAW. The same applies to Tier1 and Tier2 administrators. Each one must use the appropriate account and PAW for their daily tasks.
Cross Areas OR Cross Tiers is not permitted within the model, and it must be avoided by any means. So returning to our previous example, the Tier1 administrator must be using a Tier 1 PAW in order to manage Tier1/Servers. In the event he needs to administer tier2 assets, then he must make the switch to Tier2.